Comparing DeCC Technologies - Is MPC the Most Balanced Approach for Blockchain Privacy and Performance?
Decentralized Confidential Computing technologies like MPC and ZK aim to make blockchains more secure at scale, but how exactly do they work?
- Published:
- Edited:
Terms like ZK-Proofs, Fully Homomorphic Encryption (FHE), and Multi-Party Computation (MPC) are often thrown around in the crypto space. Yet, many crypto enthusiasts are still scratching their heads wondering how these technologies can actually improve blockchain networks and the applications they support.
Thanks to the endless rollout of ZK-rollup Layer-2s in the Ethereum landscape, ZK-proofing is probably the best-known DeCC (Decentralized Confidential Computing) technology in the crypto industry. However, that doesn’t necessarily mean it’s the most effective.
What are the pros and cons of various DeCC approaches and how are they adapted for different outcomes?
DeCC Technologies: A Comparison
When it comes to confidential computing, there’s no one-size-fits-all approach that ticks every box. Similar to Vitalik Buterin’s famous Blockchain Trilemma, DeCC technologies often outperform in one area at the expense of another.
For example, Trusted Execution Environments (TEE) are hardware-based solutions that are arguably more secure and scalable than software-based solutions.
However, this is something of a double-edged sword. TEEs lack the flexibility of software-based DeCC technologies and rely on hardware providers and manufacturers.

Which privacy-enhancing technologies are best suited for general confidential computing needs?
Multi-Party Computation (MPC)
MPC is a cryptographic technique that allows multiple parties to compute a function while keeping said inputs private and confidential. It enables participants to collaborate on calculations without revealing their individual data to each other and any lurking third party.
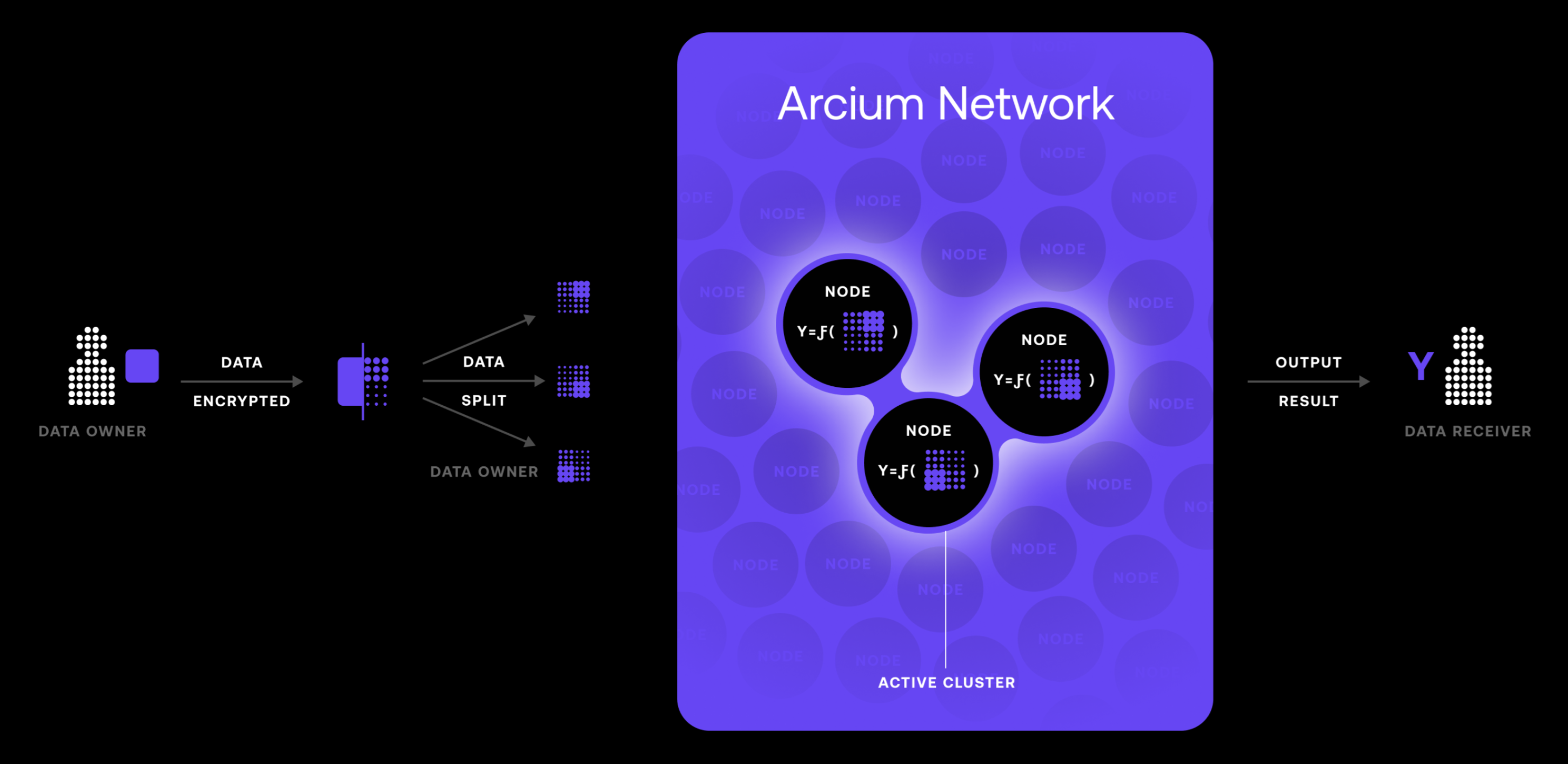
MPC ensures both privacy and accuracy, even if some collaborators try to deviate from the protocol. This DeCC approach is particularly useful in scenarios where multiple entities need to perform computations and access sensitive data, such as in financial services or secure voting systems.
Pros
-
Enhanced security through distributed key management
-
Eliminates single points of failure
-
Maintains privacy of individual inputs
-
Flexible for various applications
Cons
-
Can be computationally intensive
-
May introduce latency in transactions
-
Requires coordination among multiple parties
Trusted Execution Environments (TEE)
TEEs are secure areas within a processor that ensure the confidentiality and integrity of code and data held within. They provide a hardware-based isolated execution environment that protects sensitive operations from external factors, like a computer’s operating system.
In theory, TEEs offer a higher level of security than software-only solutions by leveraging hardware features to create a trusted zone for processing sensitive information.
Trusted Execution Environments are often in mobile devices, cloud computing, and other scenarios where developers require secure data processing at scale.
Pros
-
Hardware-level security
-
Faster than pure software-based solutions
-
Can handle sensitive operations in an isolated environment
Cons
-
Reliance on hardware manufacturers
-
Potential vulnerabilities in hardware implementation
-
Limited flexibility compared to software solutions
Zero-Knowledge Proofs (ZK)
One of crypto’s favorite buzzwords, Zero-Knowledge Proofs allow one party (the prover) to prove to another party (the verifier) that a statement is true without revealing any information about the content of the statement itself.
ZK proofs provide strong privacy guarantees while enabling verification of specific claims or computations. Zero-knowledge proofing offers a powerful tool for maintaining privacy during onchain interactions.
However, ZK-proof technology often relies upon a ‘trusted setup’, which requires parties to trust each other to a certain degree before generating the keys that maintain the proof system. In some ways, this eliminates the effectiveness of zk-proofing cryptography.
Pros
-
Provides strong privacy guarantees
-
Reduces the amount of data needed for verification
Cons
-
Can be computationally expensive
-
May require ‘trusted setup’ in some implementations
Fully Homomorphic Encryption (FHE)
Finally, Fully Homomorphic Encryption allows computations to be performed on encrypted data without decrypting it. With FHE, data can remain encrypted throughout the entire computation process, with the results also remaining encrypted.
This technology enables secure outsourcing of computations on sensitive data, making it particularly valuable for cloud computing and data analysis scenarios. While FHE offers high levels of data privacy, it faces significant performance challenges that limit its scalability.
Pros
-
Enables secure computation on sensitive data
-
Maintains data privacy throughout the computation process
-
Useful in cloud computing and data analysis
Cons
-
Extremely computationally intensive
-
Low scalability
At a Glance
|
Tech |
Privacy |
Performance |
Flexibility |
|
MPC |
High |
Moderate |
High |
|
TEE |
Moderate |
High |
Low |
|
ZK |
High |
Low |
High |
|
FHE |
Very High |
Low |
High |
Essentially, it boils down to this: Different DeCC technologies are better suited for different applications. FHE might be one of the most private and secure confidential computing technologies available, but it still suffers from low latency and scaling issues.
Meanwhile, TEEs are some of the most performant environments for processing computations, but their reliance on hardware means they can lack the flexibility required in a rapidly evolving industry.
All things considered, Multi-Party Computation perhaps offers the most balanced approach to decentralized confidential computing. By distributing computation across multiple inputs, MPC eliminates singular points of failure while still providing sufficient levels of performance.
MPC in Action: Arcium

Arcium, a DeCC protocol building on Solana, leverages MPC to power its secure and performant computational network.
Arcium's network consists of multiple nodes called Arx, which collectively process encrypted data using MPC protocols. This distributed architecture ensures that no single node has access to the complete dataset, enhancing security and eliminating single points of failure.
Beyond Arx nodes, Arcium also introduces MXEs, or Multiparty eXecution Environments. These MXEs serve as virtual machines for secure multiparty computations and allow developers to configure various aspects of the computation, including encryption schemas, node selection, and execution parameters.
Additionally, Arcium has developed its own native programming interface, Arcis, designed for writing secure MPC applications. It provides developers with a familiar and intuitive interface for creating privacy-preserving applications that can compute encrypted data within isolated MXEs.
The Arcium network offers customizable MPC setups, allowing users to tailor security levels, node selection, and execution protocols to their specific needs. The flexibility MPC offers makes Arcium suitable for a wide range of applications, from AI model training to medical data analysis.
Arcium leverages MPC technology across its expansive product suite to provide a powerful confidential computing platform that prioritizes privacy, security, and collaboration. Arguably one of the most well-rounded DeCC technologies available, MPC gives Arcium the flexibility, resilience, and performance required to power its growing network.
This approach positions Arcium as a key player in the decentralized confidential computing space, ensuring the protocol is well-equipped to facilitate the demands of emerging industries like DePIN, AI, and blockchain-based healthcare solutions.
Read More on SolanaFloor
Solana’s biggest governance protocol is evolving
Realms Breaks Ties with Solana Labs to Form Separate Entity
Video